If you're familiar with containerization, you've likely heard of Linux namespaces. These are a core component of containerization technology, allowing for process isolation and resource management in a containerized environment. In this post, we'll explore how containers utilize Linux namespaces, with a specific focus on Docker, and why they're essential for modern application deployment.
What are Linux namespaces?
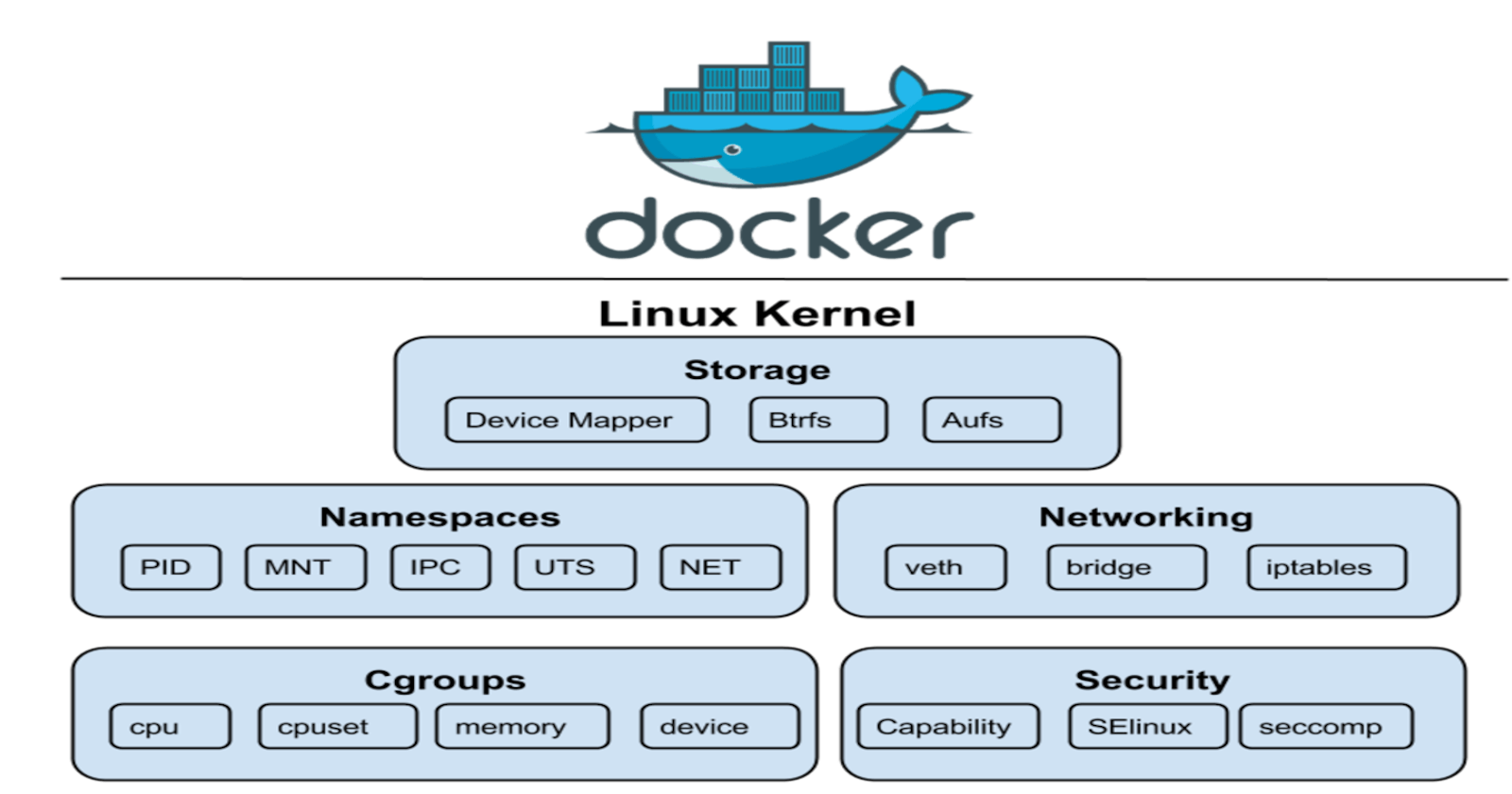
Linux namespaces are a kernel-level feature that allow processes to have their own isolated view of system resources. A namespace acts as a virtual container around a set of system resources, providing a unique identifier for each container. This enables processes running inside a namespace to see only the resources associated with that namespace, and not those in other namespaces.
Linux provides several different types of namespaces, each corresponding to a specific resource type. These include:
PID namespace: isolates processes from each other, allowing each container to have its own set of process IDs.
Network namespace: isolates network interfaces, allowing each container to have its own network stack.
Mount namespace: isolates the file system mount points, allowing each container to have its own file system hierarchy.
UTS namespace: isolates the hostname and domain name, allowing each container to have its own unique identity.
IPC namespace: isolates inter-process communication mechanisms, allowing each container to have its own shared memory and message queues.
Together, these namespaces provide a powerful toolset for containerization, enabling multiple containers to run on the same host without interfering with each other.
How does Docker use namespaces?
Docker is one of the most popular containerization platforms, and it heavily utilizes Linux namespaces to create isolated environments for running applications. When a Docker container is started, it creates a set of namespaces, each with its own unique identifier. The container's processes are then started inside these namespaces, which isolates them from other processes running on the host.

For instance, when a Docker container is started, it creates its own network namespace, which allows it to have its own network interfaces and routing tables. This ensures that the container's network traffic is isolated from other containers and the host itself. Similarly, the container's mount namespace allows it to have its own file system hierarchy, which can be completely different from the host file system.
Docker also uses other Linux capabilities, such as cgroups, to further isolate container resources and ensure that they don't interfere with other containers or the host system. This enables Docker to provide a high degree of isolation and security, while still maintaining a lightweight and efficient containerization platform.
Examples of Docker's use of namespaces
To better understand how Docker utilizes Linux namespaces, let's look at a few examples:
Network isolation: By utilizing network namespaces, Docker can isolate container traffic from the host system and other containers. This enables multiple containers to run on the same host, each with its own network stack and routing table. For instance, a web server container could be configured to listen on a specific IP address and port, without interfering with other containers or the host system.
File system isolation: Docker's use of mount namespaces allows it to provide isolated file systems for each container. This enables containers to have their own read-write file system layers, without affecting the host file system or other containers. Additionally, Docker's use of overlay file systems allows it to efficiently share file system layers across multiple containers, further reducing overhead and improving performance.
Resource management: Docker's use of cgroups, which work in conjunction with namespaces, allows it to limit container resource usage and ensure that containers don't interfere with each other or the host system. For instance, CPU and memory usage can be limited for each container, preventing a single container from monopolizing resources and affecting other containers' performance.
Advantages and limitations of using namespaces in containers
There are several advantages to using namespaces for containerization. First, they provide a lightweight way to achieve process isolation and resource management, without requiring a full-blown virtual machine. This makes containers more efficient to deploy and maintain, while still providing a high degree of flexibility and scalability.
However, there are also some limitations to using namespaces in containers. For instance, namespaces can introduce new security risks if not properly configured. A misconfigured namespace could allow a container to access resources that it shouldn't have access to, or interfere with other containers running on the same host. Therefore, it's important to carefully manage namespace configuration and security and to regularly audit the container environment for potential vulnerabilities.
Conclusion
Linux namespaces are a powerful toolset that enables containerization platforms like Docker to create isolated environments for running applications. By isolating resources such as process IDs, network interfaces, and file systems, namespaces enable containers to run multiple applications on the same host without interfering with each other. Docker heavily utilizes namespaces to provide a lightweight and efficient containerization platform, and its use of cgroups further ensures that container resources are efficiently managed.
If you're interested in containerization and modern application deployment, understanding how Linux namespaces work is essential. Hopefully, this post has provided you with a good introduction to this crucial technology and how it's utilized in Docker.